Phishing emails are fraudulent messages designed to trick you into revealing sensitive information or installing malware. Use this checklist to help identify potential phishing attempts in your work email. It’s tailored for small/medium business employees with basic to intermediate computer skills – follow these guidelines before you click or respond to any suspicious email.
Verify the Sender
- Sender’s Email Address: Check that the sender’s email address is genuine. Look for slight misspellings or odd domain names (e.g.
john.doe@yourcompany.comvsjohn.doe@yourcornpany.com)hp.com. A mismatch between the sender’s display name and the actual email address (or an unexpected external domain) is a red flagphishlabs.com.
🛠️ Tools I Personally Deploy (and Why)
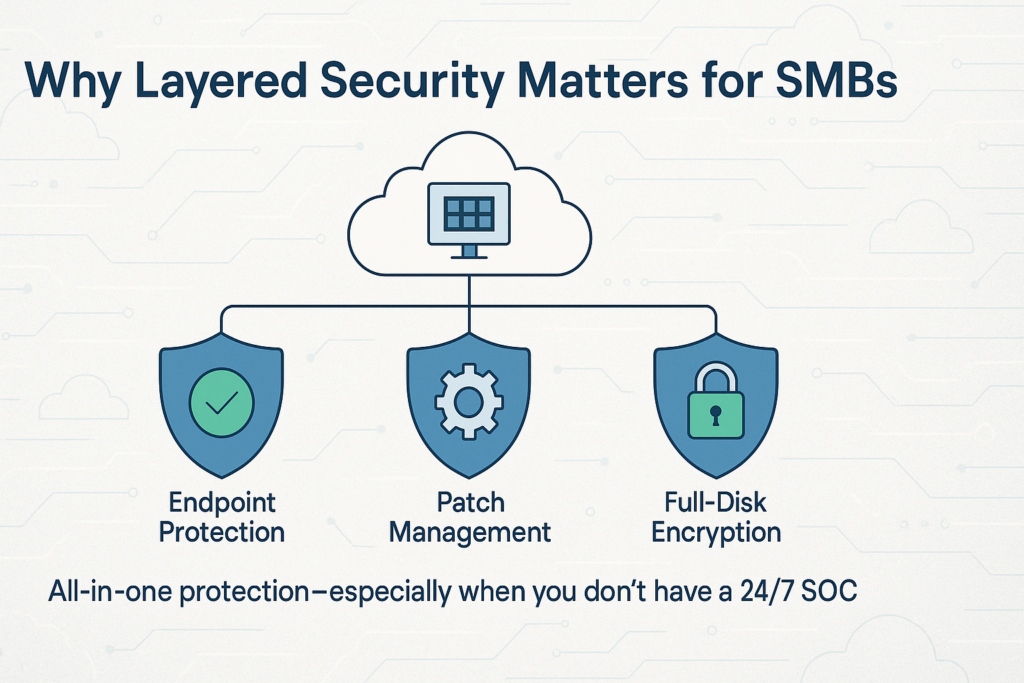
Most SMBs don’t have a 24×7 SOC, so layered defense matters. My go‑to bundle combines endpoint protection with easy patching and full‑disk encryption—all managed from one cloud console:
Why I like it: light agent, sane pricing, and it saved one client after a click‑happy intern downloaded what turned out to be Emotet. Zero infections, zero overtime.
👉 Check out Bitdefender GravityZone for SMBs
Examine Email Content
- Beware of Fake Branding: Don’t trust an email just because it includes official logos or branding – scammers can easily spoof logos and email layouts to look authentic. A professional appearance alone doesn’t guarantee the email is legitimate.
- Generic or Impersonal Greeting: Phishing emails often use a generic greeting or no name at all. Be cautious if an email starts with something like “Dear Customer” or “Sir/Madam” instead of your name. Legitimate senders usually address you personally.
- Urgent or Threatening Language: Be wary of messages that pressure you to act immediately or warn of dire consequences (e.g. “Your account will be closed today if you don’t respond!”). Scammers use urgent, threatening language to scare you into quick action without thinking.
- Poor Grammar or Spelling: Many phishing emails contain spelling mistakes, odd phrasing, or grammatical errors. Professional organizations typically proofread communications, so obvious errors can be a sign of a scam.
- Too Good to Be True Offers: Be skeptical of unsolicited emails promising rewards like prizes, refunds, or exclusive offers out of the blue. If it sounds too good to be true, it probably is. Scammers lure victims with enticing promises to get them to click links or give up info.
Check Links and Attachments
- Inspect Links Before Clicking: Before you click any link, hover your mouse over it (without clicking) to preview the URL. Ensure the link’s destination looks legitimate and is spelled correctly. If the URL is odd, doesn’t match the context of the email, or is a shortened link you don’t recognize, do not click. Instead, navigate to the website by typing the known web address into your browser.
- Be Wary of Attachments: Treat email attachments with caution. Do not open attachments from unknown senders, and be careful even with unexpected attachments from people you do know. Common malware file types include
.exe,.zip, or unusual document formats. If you’re not expecting an attachment, verify with the sender through a separate communication channel. When in doubt, scan attachments with up-to-date antivirus software before opening them.
Be Cautious with Requests
- Requests for Sensitive Info: Any email asking you to provide sensitive data (passwords, banking details, Social Security numbers, etc.) is highly suspiciousphishlabs.com. Legitimate companies and IT support will never ask for your password or similar information via email. Never email confidential information unless you have absolutely verified the recipient’s identity and legitimacy.
- Unusual or High-Value Requests: Be alert to strange requests, especially those urging urgent financial actions. Scammers may impersonate a colleague or executive (e.g. your CEO) asking for things like wire transfers, gift card codes, or confidential files on short notice. If an email from a coworker or boss seems out of character or asks for an unusual favor, double-check it. Call the person at a known number or confirm in person to ensure the request is legitimate.
Watch on YouTube
When in Doubt, Verify and Report
- Verify via Trusted Channels: If you suspect an email might be a phish, do not click links or reply. Instead, verify the message through a known trusted method. For example, call the sender using an official phone number (not one provided in the email) or send a fresh email to their known address (not by replying) to confirm they actually sent you the message. This outside confirmation can save you from a potential scam.
- Report Suspicious Emails: If an email looks like a phishing attempt, report it according to your company’s policy. Use your email client’s “Report phishing” button or immediately alert your IT department or security team. Reporting helps protect others by enabling IT to block similar emails and inform staff. When you report a phish, do not forward it to colleagues (to avoid accidental clicks); let the experts handle it.
By following this checklist every time you encounter a questionable email, you can greatly reduce the risk of falling victim to phishing attacks. Stay vigilant and when in doubt, always err on the side of caution.