Introduction
Modern workplaces increasingly permit BYOD (Bring Your Own Device) – allowing employees to use personal laptops, smartphones, USB drives, and other devices for work. This practice is widespread: over 60% of organizations now allow personal devices for work tasks, and roughly two-thirds of employees use their own devices at work.

Companies embrace BYOD for its convenience, cost savings, and productivity benefits – employees are already familiar with their own tech, and businesses save on hardware costs, while morale and efficiency often improve. However, these advantages come with serious security challenges. Experts warn that BYOD can lead to data theft, malware infections, and other risks that disrupt operations and leak sensitive data. The following report details the key security issues companies face with BYOD and how to mitigate them, including real-world incidents and best practices encompassing technical solutions and organizational policies.
Watch on Youtube
Key Security Risks When Using Personal Devices
When employees use unmanaged personal devices (USB flash drives, phones, laptops) for work, several security risks arise:
- Data Loss and Leakage: One of the biggest concerns is losing control of sensitive company data. Personal devices may store corporate emails, client lists, or confidential files outside the secure company network. If such a device is lost, stolen, or accessed by unauthorized persons, the data can be exposed. For example, an employee’s personal device containing customer data could be stolen during a break-in or lost offsite, leading to a costly data breach. Employees might also save work files to unsecured personal cloud apps or USB sticks, which can be misplaced or accessed by family/friends, unintentionally leaking information. Without proper safeguards (like encryption or access controls), any data on a personal device is at risk if the device falls into the wrong hands. In short, BYOD blurs the boundary of data control, increasing the chance that sensitive information escapes the organization’s protection.

- Malware Infections and Malicious Apps: Personal devices are often not as tightly secured or monitored as corporate-issued devices, making them more susceptible to malware. Employees can install apps or download content freely on their own device – some of which may hide spyware, ransomware, or viruses. Not all apps are what they appear, and malicious applications can hijack a user’s phone or laptop, stealing data or spying on communications. In a 500-SME survey, malware was the most common security incident after adopting BYOD – affecting 65% of those companies (with viruses impacting 42%). This indicates how BYOD can introduce malware into business networks. A personal device may already be infected without the user realizing. Moreover, if the device’s operating system or apps are outdated and unpatched, it’s at even greater risk – many of the most vicious mobile malware strains prey on outdated OS vulnerabilities. Once a compromised personal device connects to company systems (or syncs files via a USB), the malware can spread to the corporate network or access protected data. This vector was dramatically demonstrated in the U.S. Department of Defense breach of 2008, where a single infected USB drive plugged into a military laptop unleashed a worm that spread undetected through classified networks. Such examples underscore that malware introduced via BYOD can lead to major breaches.
- Insecure Access (Networks and Authentication): Employee-owned devices may not adhere to the same network security practices as corporate ones. For instance, users might connect to work systems from unsecured public Wi-Fi at airports or cafes, or use home networks with weak security. This opens the door to eavesdropping and man-in-the-middle attacks. If an employee accesses corporate email or cloud apps on a public hotspot without a VPN, an attacker could intercept that communication and potentially steal credentials or data. Additionally, personal devices might not enforce strong authentication – some employees reuse weak passwords or have no PIN on their smartphone. If BYOD devices lack robust login security (e.g. device passcodes, biometrics, or multi-factor authentication), unauthorized access becomes easier. An attacker who guesses or obtains a weak password could directly log into corporate apps from the employee’s device. Mixing personal and work usage exacerbates this: employees may inadvertently expose work accounts when using personal services. They might click phishing links on personal email or social media that compromise the device, and by extension the saved corporate logins. In one study, 84% of people admitted using the same smartphone for both personal and work tasks – such cross-usage means if the personal side is compromised, work data is at risk. Without secure network connections and strong authentication, BYOD can become an insecure gateway into company systems.

- Insufficient Policy Compliance and Shadow IT: BYOD can lead to situations where IT has little visibility or control over devices handling company data. If an organization lacks a clear BYOD security policy (or doesn’t enforce it), employees may unknowingly engage in risky practices. This includes “shadow IT,” where staff use unapproved apps or cloud services for work because it’s convenient. For example, an employee might use a personal Dropbox or Google Drive to transfer work files, one of which was later accessed by a former employee after leaving, constituting a data breach. Similarly, employees may disable security features on their devices (e.g. jailbreaking a phone or turning off auto-updates) for personal reasons, making the device more vulnerable. Without guidelines, they might also share their device with family members or friends, exposing corporate data to people outside the company. Disgruntled or departing employees with company data on their personal device could retain or misuse that data if access isn’t quickly revoked. In summary, without strict BYOD policies and oversight, personal devices can easily become a weak link through user negligence or intentional bypass of security measures.

- Lost or Stolen Devices: The portability of personal devices – a key benefit – is also a major security risk. Laptops, smartphones, and USB flash drives are small and easy to lose or steal. If an employee’s device containing work information is lost on a train or stolen from a car, the company may suffer a data breach. This is not a hypothetical concern; it happens frequently across industries. A lost unencrypted USB drive led to a significant breach at Heathrow Airport – an employee misplaced a thumb drive containing over 1,000 confidential files (including names, birthdates, and passport numbers of staff). A member of the public found it and viewed the sensitive contents at a library, leading to regulatory fines for the airport. This breach underscored the danger of uncontrolled USB devices and lack of encryption. A basic policy requiring encryption on all removable media could have prevented outsiders from reading the drive’s files. In response, Heathrow tightened its information security policies and training. Many other companies also instituted USB device bans or encryption mandates after similar scares, recognizing portable drives as a major BYOD threat vector.

Summary of Key BYOD Risks: As outlined above, allowing personal devices introduces threats of data leakage, malware, insecure network access, lack of oversight, and device loss. Table 1 summarizes these risks and their potential impact, along with real examples:
Key Security Risks of Employee BYOD and Their Impact
| Risk | Description | Real-World Example |
|---|---|---|
| Data Leakage | Sensitive corporate data can be exposed via personal devices. This may occur through lost/stolen devices or unauthorized data transfers (e.g. copying files to personal apps). | Lost USB drive at Heathrow Airport: Exposed 1,000+ confidential files (names, passport numbers, etc.) when found by a stranger; data was unencrypted. |
| Malware Introduction | Unmanaged devices may carry malware or rogue apps that infiltrate the corporate network. Personal laptops/phones lacking enterprise-grade antivirus or patching can become a trojan horse for infections. | Agent.BTZ Worm (U.S. DoD, 2008): A malicious USB plugged into a military laptop unleashed a worm that spread to classified networks – one of the worst breaches in U.S. military history. |
| Insecure Access | BYOD users might connect via public Wi-Fi or use weak device passwords. Attackers can intercept unsecured communications or exploit poor authentication to access company systems through a personal device. | Public Wi-Fi Eavesdropping: An employee’s phone on open Wi-Fi without a VPN can be sniffed by attackers, potentially capturing corporate login credentials. |
| Lack of Oversight (“Shadow IT”) | Personal device use can bypass IT controls. Without strong BYOD policies, employees may use unapproved apps/cloud services, delay security updates, or share devices with others – creating compliance gaps and vulnerabilities. | Medical Records Breach (Healthcare): A clinic employee copied ~6,000 patient records onto a personal USB drive and lost it, unknowingly violating policy. The breach led to her firing and a HIPAA investigation. |
| Lost or Stolen Device | Portable personal devices can be lost or stolen, potentially exposing any confidential data stored on them. Without encryption or remote wipe, the data is freely accessible to whoever gains possession. | Stolen Hospital Laptop: A university hospital was fined $1.5M after a research laptop with unencrypted PHI was stolen, violating HIPAA for not securing mobile devices. Many similar incidents across industries show the high cost of lost devices. |
(Major risks introduced by BYOD, with examples of incidents. These range from data leaks due to lost media, to malware infiltrations and policy lapses. Each risk requires targeted controls to mitigate.)
BYOD can dramatically expand an organization’s attack surface. In fact, studies have directly linked BYOD usage to higher rates of security incidents. One UK survey of SMEs found a positive correlation between BYOD and cyber incidents: 61% of companies experienced a security incident after introducing BYOD. The incidence rate climbed to 94% for medium-sized firms (101–250 employees) with BYOD. The types of incidents reported ranged from malware outbreaks and phishing attacks to actual data theft. Real-world breach examples span multiple industries – from finance to healthcare to government – and often trace back to a personal device as the point of failure. Below are a few notable BYOD-related breaches that underscore the consequences of these risks if not properly managed.
Real-World BYOD Breach Incidents
Organizations of all sizes have suffered breaches due to employee-owned devices. These cases highlight how BYOD risks can translate into tangible damage:
- Cryptocurrency Exchange Breach (Bithumb, 2017): In 2017, South Korean crypto-exchange Bithumb disclosed that about 30,000 customers’ personal details were exposed when an employee’s home computer (used for work) was hacked. Attackers stole names, phone numbers, and email addresses, which were later used in follow-on attacks (like voice phishing) to target Bithumb’s users. Because the employee had been storing customer data on a personal PC outside the company’s direct control, Bithumb’s lack of a strict BYOD policy directly contributed to the breach. The incident serves as a caution that BYOD policies shouldn’t just cover phones – even personal home laptops/desktops with company data pose a risk. After the breach, security experts noted that any cost savings from BYOD were dwarfed by the financial and reputational damage caused by such data loss.

- Heathrow Airport USB Breach (2017): A high-profile data leak occurred at Heathrow Airport when an employee lost an unencrypted USB flash drive containing sensitive security data. The drive, which held 76 folders including personal information on aviation security staff, was found by a random passerby on the street. Before it was returned, the finder viewed some of the classified contents at a public library. The data included names, dates of birth, passport numbers, and security details – none of it password-protected or encrypted. The UK Information Commissioner’s Office fined Heathrow for failing to secure the personal data and for inadequate training (it was revealed only 2% of staff had been trained in data protection at the time). This breach underscored the danger of uncontrolled USB devices and lack of encryption. A basic policy requiring encryption on all removable media could have prevented outsiders from reading the drive’s files. In response, Heathrow tightened its information security policies and training. Many other companies also instituted USB device bans or encryption mandates after similar scares, recognizing portable drives as a major BYOD threat vector.

- Healthcare Data Loss Incidents: The healthcare sector, with its strict privacy regulations, has seen numerous BYOD-related breaches. In one case, a teaching hospital and affiliated medical practice were fined by U.S. regulators after a physician’s unencrypted personal laptop containing patient records was stolen. The investigation found they had no effective BYOD security controls or encryption, violating HIPAA’s Security Rule. In another incident, an employee at a health department copied thousands of patient records onto a personal USB drive which was then lost, resulting in a reportable data breach and employee termination. These cases illustrate that BYOD without proper safeguards can directly lead to regulatory non-compliance (e.g. HIPAA, GDPR) and heavy penalties. Healthcare organizations now often ban personal USB storage and require any BYOD access to patient data to be through encrypted, managed apps only.

- SME “Shadow IT” Breaches: Smaller companies are not immune. A survey of 500 SMEs found that after adopting BYOD, a staggering 70%–94% experienced security incidents depending on size. One contributing factor is shadow IT and lack of centralized control – e.g. employees at a marketing firm using personal Dropbox accounts to share client files, one of which was later accessed by a former employee after leaving, constituting a data breach. In another SME example, an employee’s personal smartphone infected with malware was unknowingly syncing to the corporate network; the malware helped attackers exfiltrate proprietary data. These “everyday” incidents might not make headlines, but they collectively cost businesses in downtime, lost data, and recovery expenses. For instance, malware and ransomware introduced via an employee’s unchecked device can result in days of system outages or expensive clean-up. The high incident rates among BYOD-friendly SMEs emphasize that without proper management, BYOD will lead not just to one-off breaches, but a sustained increase in security events.

Each of these cases could likely have been prevented or mitigated through stronger controls and user awareness. In the next section, we outline best practices – both technical and organizational – that companies should implement to manage BYOD risks. Adopting these measures can allow companies to enjoy the benefits of BYOD (flexibility, productivity) while maintaining security and compliance across industries.
Best Practices for Managing BYOD Risks
To safely enable BYOD, organizations must take a multi-layered approach combining technical solutions and clear policies. The goal is to secure both the devices and the data they access, without overly hampering employee productivity. Below are key best practices and recommendations to manage BYOD security risks.
Technical Solutions and Security Controls
Implementing the right technical controls can drastically reduce the risks posed by employee devices. Important measures include:
- Mobile Device Management (MDM) Software: An MDM system is essential for enrolling personal smartphones/tablets and applying security policies remotely. With MDM, IT can enforce device PIN/password requirements, encryption, and app restrictions on BYOD hardware. Crucially, if a device is lost or an employee leaves, MDM allows the company to remotely wipe corporate data from the device. For example, a policy can mandate that any BYOD phone used for work email must be managed by the company’s MDM – if the phone is reported lost, the IT admin can send a command to erase all company email and files on that phone. MDM tools also enable pushing security updates and configurations to ensure devices stay compliant. This central management is the backbone of technical BYOD security, giving some control back to IT over otherwise unmanaged devices.

- Endpoint Protection (Anti-Malware and Device Security): All BYOD endpoints that connect to company resources should have up-to-date anti-malware protection. This includes antivirus or EDR (Endpoint Detection & Response) software on laptops and possibly mobile threat defense apps on phones. Scanning personal devices for viruses before they access the network can catch threats early. In addition, enabling personal firewalls and leveraging OS security features provides baseline protection. Companies can also use network access control (NAC) or endpoint compliance checks – for instance, only allow a BYOD laptop on the corporate VPN if it has current antivirus definitions and patches installed. Monitoring tools should be in place to detect any suspicious activity from BYOD devices on the network. By actively scanning and monitoring BYOD endpoints for malware, IT can contain infections before they spread. Some organizations even sandbox BYOD devices on a separate network segment so that if a compromise occurs, it can’t easily propagate to critical systems.
- Data Encryption (Device & Network): Encryption is a must-have safeguard for BYOD data protection. First, devices themselves should use full-disk encryption – modern smartphones (iOS, Android) and laptop OSs support this, but it may need to be enforced. Encryption ensures that if a device is lost or stolen, the data remains unreadable without the decryption key/password. For instance, a USB incident avoided disaster because the drive was encrypted and password-protected, illustrating the value of strong encryption (though relying on users to encrypt manually is risky – it should be automatic via policy). Secondly, companies should require that all network traffic from personal devices be encrypted in transit. The primary way to do this is by using a VPN (Virtual Private Network) or secure remote access gateway. A VPN client on the BYOD device will encrypt all its communications back to the company network, preventing eavesdropping on public Wi-Fi. Many MDM suites can force a device to only reach corporate services through an approved VPN. Additionally, end-to-end encryption should be enabled for sensitive applications (email, messaging, etc.). Encrypted data, both at rest and in transit, significantly reduces the impact of interception or loss – even if an attacker obtains the files, they can’t read them without the keys. As a best practice, businesses should also back up critical data from BYOD devices to secure cloud or server locations (or ensure that data is primarily stored in the cloud), so that loss of a device doesn’t mean loss of the data.
- Application Control and Containerization: To tackle the mingling of personal and work usage, companies can use containerization or app sandboxing technologies. Containerization creates a separate, encrypted workspace on the personal device for all company apps and data. For example, a “work profile” on Android or iOS can isolate corporate email, documents, and messaging communications from the user’s personal apps. This way, the company can manage and wipe the container without affecting personal files. It also prevents data from being copied between work and personal domains (no accidentally emailing a client file via personal Gmail, for instance). Another aspect is controlling which apps can be used for work. Organizations should provide an enterprise app store or list of approved apps – ensuring employees download vetted applications for work tasks rather than risky third-party apps. Where possible, limit the installation of apps that demand excessive permissions or are known to be insecure. At minimum, educate users only to install apps from official app stores and to beware of “lookalike” malicious apps. By using app segregation, Mobile Application Management (MAM), and containerization, companies keep a firm boundary between business and personal data, greatly reducing the risk of accidental leaks. In practice, this might mean using specialized secure apps for email, file access, and CRM on BYOD devices – those apps enforce encryption and policy within themselves, independent of the user’s other apps.

- Strong Authentication and Access Management: Strengthening login security for BYOD devices and services is critical. All remote or mobile access to corporate systems should require strong authentication, preferably multi-factor authentication (MFA). MFA ensures that even if a password is compromised (which is more likely on personal devices due to phishing or reuse), an attacker cannot access the account without a second factor (like a one-time code or biometric check). Many breaches, such as the intercept of credentials on public Wi-Fi, could be foiled by MFA. Companies should integrate MFA into email, VPN, cloud apps – any resource accessible via BYOD. Additionally, enforce basic device access security: require that employees set a device lock (PIN/password or biometric) and configure auto-lock timeouts. Simply having a lock screen can prevent a thief from immediately accessing data on a lost device. Beyond user authentication, practice the principle of least privilege: limit what data and systems a BYOD user (or device) can reach. Use role-based access controls so that employees on personal devices only access the minimum necessary data. Network segmentation also plays a role – if a BYOD device does not need to be on the same network as critical servers, keep it isolated in a guest or limited network zone. In summary, tighter access controls (MFA, device locks, segmented networks) add layers of defense in case a personal device or its credentials are compromised.
- Data Loss Prevention (DLP) Tools: To prevent and detect data leaks from BYOD endpoints, organizations can deploy DLP solutions that monitor data flows. DLP software can be configured to flag or block certain activities – for example, copying files to a USB drive, or emailing a client list outside the company. Some advanced DLP systems extend to mobile devices or integrate with cloud services, helping enforce that sensitive files aren’t uploaded to personal accounts. While DLP on BYOD devices can be challenging (since you may not have full control of the device), focusing on DLP at the network or cloud level is very effective. For instance, if an employee on a personal laptop tries to download an entire customer database, a DLP rule could detect that unusual volume and stop it, or at least alert security. Similarly, DLP can prevent copying corporate emails or chat messages into unauthorized apps. Combined with containerization, DLP forms a safety net ensuring that even if employees attempt to move data out of authorized channels, the system intervenes. It’s a valuable tool for compliance – helping organizations prove they have measures to prevent data exfiltration from personal devices.

The above technical measures can be summarized as layers that protect device, network, applications, and data. Table 2 provides a quick overview of key tools/solutions and how they address BYOD risks:
Technical Controls for Securing BYOD
| Technical Solution | Purpose / Benefit | Addresses |
|---|---|---|
| Mobile Device Management (MDM) (e.g. Intune, MobileIron) | Enrolls personal devices under company oversight. Enforces security policies (passwords, encryption, app install rules) and enables remote wipe of corporate data if a device is lost or when an employee departs. Also allows pushing updates and restricting device features (like disabling USB storage or camera if needed). | Lack of control; Data leakage (lost devices); Unpatched OS. |
| Endpoint Security (EPP/EDR) (Antivirus, anti-malware, mobile threat defense) | Detects and blocks malware on BYOD endpoints. Scans files and apps for threats, preventing viruses or spyware on a personal device from infiltrating the corporate network. Modern EDR can also monitor behavior and isolate compromised devices. | Malware infections; Unauthorized access (if keyloggers/trojans are present). |
| Full-Device Encryption | Encrypts storage on BYOD devices (phones, laptops) so that data remains unreadable if the device is lost or stolen. Often enforced via MDM or OS policy. Ensures that even physical possession of the device doesn’t equate to data access. | Data loss from theft; Compliance (protects PII/PHI on devices). |
| Virtual Private Network (VPN) | Encrypts network traffic from the personal device to the company network. This protects against eavesdropping on public Wi-Fi and ensures secure access to internal systems. Many organizations require VPN for any remote connection. | Insecure Wi-Fi/network attacks; Data interception. |
| App Containerization (Work Profiles, Secure Containers) | Segregates corporate apps and data into a managed container on the BYOD device. Provides a dedicated encrypted storage area and separates work vs. personal use (preventing data mix-ups). IT can wipe the container independently. | Data leakage (mixing work/personal); Policy non-compliance (unapproved apps can’t access work data). |
| Enterprise App Catalog | Offers employees a selection of pre-approved, secure applications for work (email, messaging, file sharing, etc.). Steers users away from risky apps and reduces “shadow IT.” May integrate with SSO for convenience. | Shadow IT; Malicious apps. |
| Multi-Factor Authentication (MFA) | Requires a second factor (OTP code, authentication app, biometric) for accessing company accounts. Even if a password is stolen, an attacker can’t log in without the MFA token. Greatly reduces account takeovers. | Account compromise; Unauthorized access through stolen credentials. |
| Network Segmentation & NAC | Limits BYOD devices to specific network segments/VLANs and uses Network Access Control to check device compliance on connect. An unpatched or unknown device can be quarantined from core systems. | Spread of malware; Unauthorized access to sensitive internal servers. |
| Data Loss Prevention (DLP) | Monitors and controls data transfers from BYOD endpoints or networks. Can block copying of sensitive files to external drives or personal cloud accounts. Alerts security teams of unusual data access or exfiltration attempts. | Data leakage (intentional or accidental); Insider misuse. |
(Key technical tools for BYOD security and the risks they mitigate.)
No single tool is a silver bullet – instead, layers of defense should be applied. For example, if a user’s personal laptop is infected by malware, endpoint antivirus might catch it; if it doesn’t, network segmentation could stop the malware from reaching a critical server; and if that fails, DLP might detect unusual data exfiltration. Meanwhile, strong authentication and encryption would ensure that even in the worst case, the damage is limited. By combining these technologies, companies create a robust shield around BYOD usage.
Organizational Policies and Strategies
Technology alone won’t secure BYOD if users are careless or unaware of their responsibilities. Thus, organizational measures and a strong security culture are equally important:
- Establish a Clear BYOD Policy: Every organization should have a formal BYOD policy that employees must read and sign before using personal devices for work. This policy sets the ground rules: which devices and operating systems are permitted, what security measures must be in place, and what actions are prohibited. A comprehensive BYOD policy typically covers device requirements (e.g. up-to-date OS, mandatory pin lock), acceptable use (e.g. no connecting to public Wi-Fi without VPN, no installation of unapproved apps that access work data), data handling guidelines, and the company’s rights (such as the right to wipe a lost device or to disconnect devices that are compromised). It should also address compliance issues – for instance, if the company must be able to retrieve work-related records on the device for legal or audit purposes. By clearly documenting these expectations, the policy ensures employees understand the security implications of BYOD. In essence, it creates a contract: employees get the convenience of BYOD, and in return they agree to follow security best practices and allow certain controls. Regularly review and update this policy as new threats or technologies emerge. Communication is key – make sure the policy isn’t just a document on file but is actively explained and reinforced.
- Employee Education and Training: Even the best policy won’t be effective if employees aren’t properly educated on it. Conduct regular training and awareness programs focusing on BYOD security. Training should include practical guidance on topics like: how to recognize phishing attempts on mobile devices, the importance of not clicking suspicious links or downloading unknown apps, safe use of Wi-Fi (using VPNs), how to create strong passwords or passphrases, and what to do if a device is lost or stolen. For example, employees should know the procedure to report a lost device immediately so IT can initiate a remote wipe. Emphasize real-world scenarios and consequences – users tend to be more careful if they understand, for instance, that a stolen phone with no passcode could give away all their work emails. Encourage a culture where security is “front of mind” even when employees are using their own phones or laptops. Some companies incorporate phishing simulations or send periodic security tips to keep awareness high. Remember that user negligence is often the weakest link, so educating users can prevent many mistakes.

- Enforce Compliance and Accountability: Having policies and educating staff is necessary, but ensuring compliance is the next step. Clearly communicate that BYOD is a privilege that comes with responsibilities – and that there will be consequences for willful non-compliance (especially for sensitive industries, regulators expect enforcement). IT departments should have a way to audit or verify compliance periodically. For instance, require BYOD users to install an MDM agent; if a device does not check in or is detected jailbroken, automatically restrict its access. Some organizations perform random compliance checks – e.g. verifying a sample of devices to ensure encryption is enabled and no prohibited apps are present. Include BYOD scenarios in your internal audits or risk assessments. It’s also important to get executive buy-in so that managers reinforce the message and users don’t feel they can bypass rules with manager approval. Additionally, incorporate BYOD into the onboarding and offboarding process: when an employee joins, ensure they accept the BYOD terms and set up their device correctly; when they leave, make sure all corporate access is removed from their personal devices (accounts disabled, device wiped if necessary). Accountability can be fostered by making it clear that while the company will do its part (provide tools and support), the employee is expected to do theirs (maintain the required security posture on their device). This partnership approach helps maintain a balance of trust and verification.
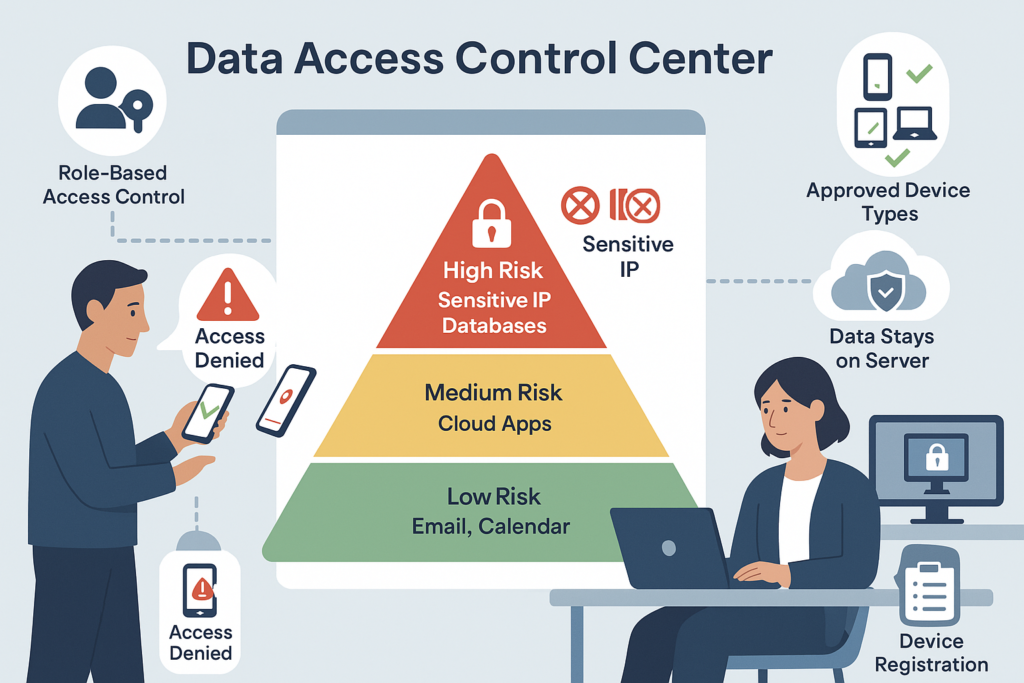
- Segment and Limit Data Access Based on Risk: Not all data and systems are appropriate for access via personal devices. Classify your data and decide what level of BYOD access is acceptable for each category. For example, a company might allow email and calendar access on any personal phone, but require a higher bar (or disallow BYOD) for highly sensitive databases or intellectual property repositories. Implement role-based access control such that employees on BYOD only get the data they absolutely need – this limits potential exposure. Moreover, consider using virtual desktop or application virtualization for higher-risk access. Instead of storing data on the BYOD device, the user could remote into a secure virtual desktop environment (VDI) or use cloud apps where data stays on the server. This way, the personal device is essentially a screen/keyboard and the data never actually resides on it. If the risk of local data is too high, this “virtual BYOD” approach can be a safer alternative. The organization can also maintain a list of “approved” BYOD device types or require registration of devices, so it knows exactly which personal devices are accessing what. Ultimately, by limiting BYOD to appropriate contexts and segmenting access rights, companies reduce the blast radius of any one device’s compromise.
- Incident Response Planning for BYOD: Incorporate personal devices into your company’s incident response plan. When a security incident occurs, it’s important to quickly determine if a personal device was involved or affected. Plan out procedures for common BYOD incidents: e.g., lost device response (who should the employee notify, how will IT wipe the device or kill its VPN access, do you also change the user’s passwords as a precaution?), or malware infection on BYOD (do you have the user disconnect immediately, bring the device in for analysis, etc.). Define responsibilities – employees should know it’s their duty to report incidents immediately without fear of blame, and IT/security need protocols to contain threats from BYOD. Regular drills or simulations can include scenarios like “employee’s personal laptop that had access to the network appears to be compromised by ransomware” to test the response. Having a plan ensures that mistakes or attacks involving BYOD are handled swiftly and correctly, minimizing damage. For instance, one SME credited an incident response plan for quickly isolating an employee’s virus-infected personal device before it could spread, significantly reducing downtime. Business continuity plans should also assume that some employees might suddenly lose the use of their BYOD devices (after a wipe or quarantine) – have backup options if needed (such as spare company devices or the ability to rapidly revoke credentials). In summary, being prepared for BYOD-related incidents can turn a potential crisis into a manageable event.

- Foster a Security-Conscious Culture: Beyond formal rules, strive to create a workplace culture where security is part of everyone’s job – especially in the context of BYOD. Encourage employees to view their personal device through the same lens as a company device when it’s being used for work. This means, for example, they keep software updated, they avoid risky behavior (like installing pirated software that could carry malware), and they respect the need for company oversight on certain aspects of the device. Leadership should model this behavior too; if executives use their own phones, they must adhere to the policies, sending a message that no one is exempt. You can also incentivize good behavior – some companies offer to subsidize a portion of the phone bill or device cost for employees who opt into BYOD and follow all the security requirements, essentially rewarding them for maintaining a secure device. When new threats or BYOD-related scams arise, promptly alert your employees and give them guidance on what to do. The idea is to create shared ownership of security: IT provides the tools and knowledge, and employees take it seriously and apply it daily. Over time, this reduces risk more than any one technology, because a vigilant user is much harder for attackers to exploit. As a simple example, an employee who is security-conscious will think twice before plugging in an unknown USB drive they found (preventing a potential attack) and will ensure their own USB drives are encrypted. Such habits, once ingrained, greatly strengthen the overall BYOD security posture.
By combining these organizational strategies with the technical controls from the previous section, companies can build a robust BYOD program. Table 3 below summarizes some of the key policy-based practices and how they help mitigate BYOD risks:
Organizational Best Practices for BYOD Security
| Policy/Practice | Description | Security Benefit |
|---|---|---|
| BYOD Security Policy | Written guidelines defining allowed devices, required security measures (passwords, updates, encryption), and user responsibilities. Users must agree to monitoring and remote wipe if needed. | Sets clear expectations; provides legal and security framework for BYOD usage. Reduces policy violations and uncertainty. |
| User Training & Awareness | Regular training on BYOD risks (phishing, unsafe Wi-Fi, malicious apps) and best practices for securing personal devices. Ongoing reminders and support resources for employees. | Reduces human error (the cause of many BYOD incidents). Educated users are less likely to fall for scams or mishandle data. |
| Onboarding/Offboarding Procedures | Processes to register personal devices when an employee joins (including installing MDM, etc.) and to remove access when they leave. May include an exit checklist to wipe corporate data from BYOD devices. | Ensures no device is unknowingly accessing corporate data, and that ex-employees don’t retain access. Closes the loop on device lifecycle. |
| Access Control & Least Privilege | Limit data access on BYOD to what’s necessary for the role. Use read-only access or virtual app sessions for sensitive data where possible. Implement MFA for all remote access. | Minimizes impact if a BYOD device is compromised – attacker cannot escalate beyond that user’s limited privileges. MFA thwarts many external attacks. |
| Regular Compliance Checks | Periodic audits or automated checks of BYOD devices for compliance (e.g. ensuring encryption is enabled, no blacklisted apps, device has recent security patches). Non-compliant devices get quarantined or notified. | Detects and fixes insecure device settings before they cause a breach. Maintains an overall standard of security across all personal devices. |
| Incident Response Integration | Extend the incident response plan to include personal device scenarios (lost device, malware on BYOD, etc.). Train IT staff on using MDM or other tools during incidents (e.g. to remotely lock/wipe a device). | Enables swift action when a BYOD-related incident occurs, reducing response time and damage. Clearly defines roles and steps to handle BYOD security events. |
| Management Support & Enforcement | Visible support from leadership for BYOD security initiatives, and consistent enforcement of policies (no exec exceptions; consequences for deliberate non-compliance). Provide helpdesk support to BYOD users to encourage compliance (e.g. assist with setting up VPN). | Fosters a culture of security and ensures policies are taken seriously at all levels. When employees see that security is a priority for the company, they are more likely to follow suit. |
(Key organizational strategies to support secure BYOD usage.)
Conclusion
Bring Your Own Device can be a double-edged sword: it offers flexibility and productivity gains to businesses and employees, but it also introduces significant security vulnerabilities if left unchecked. Malware infections, data leaks, and unauthorized access are not abstract threats – they manifest in real breaches costing companies millions and damaging their reputation. The rise of remote work and constant connectivity has only amplified the need to get BYOD security right, as personal devices often serve as an extension of the corporate network.

The good news is that with a combination of robust technical controls and well-enforced policies, companies can reap the benefits of BYOD while minimizing risk. Real-world examples have shown that measures like encryption, MDM with remote wipe, and strong authentication can avert catastrophe (or at least greatly limit the impact) when devices go missing or come under attack. Likewise, organizations that foster user awareness and have clear response plans tend to handle BYOD incidents much more effectively than those who leave security to chance. A layered defense – sometimes characterized as a “zero trust” approach where no personal device is implicitly trusted – ensures that even if one layer fails (say an employee falls for a phishing link on their phone), other safeguards (like network segmentation and MFA) still protect the enterprise data.
In implementing BYOD security, companies should strive for solutions that are practical and user-friendly. If security measures are too onerous, employees might seek workarounds (creating new risks). Therefore, involve stakeholders in crafting the BYOD program: find the balance between security and usability. Many modern tools (cloud-based productivity suites, mobile device containers, etc.) are designed to make secure BYOD seamless – leverage these innovations. Additionally, keep policies up to date with evolving threats; what was sufficient two years ago may need revising as attackers find new ways to target mobile workers.
Across industries – be it finance, healthcare, tech, or government – the principles remain the same. Protect the data, educate the user, and prepare for the worst. A financial firm, for instance, might emphasize encryption and DLP to safeguard client information on BYOD devices, while a healthcare provider might focus on HIPAA-compliant mobile apps and strict access controls. In every case, the organizations that succeed are those that treat BYOD not as a casual convenience but as an integral part of their security architecture. As one cybersecurity expert aptly noted, the cost savings of BYOD are never worth it if they come at the expense of a major data breach. By following the best practices outlined in this report, companies can significantly reduce the likelihood of BYOD-related security incidents and confidently enable their workforce’s productivity – anytime, anywhere, on any device – but done securely.


